Overview and research
XDR vs. EDR vs. antivirus
XDR, EDR and traditional antivirus software are security solutions that are used to protect networks and individual systems from malware and other cyber threats. The different versions are suitable for different types of environments and fields of application due to their respective range of functions.
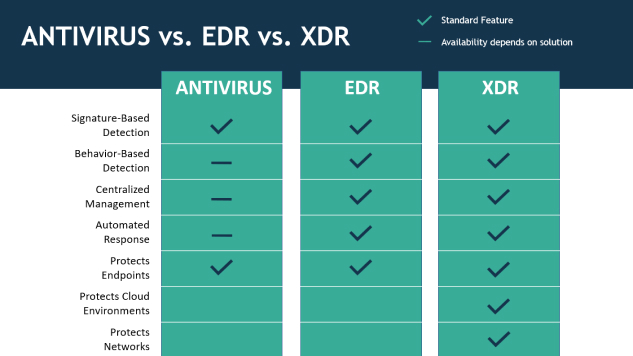
Traditional antivirus software is designed to detect and remove known malware on a system. These solutions are usually based on signature-based detection, where the files on a device are compared with a database of known malware signatures. The transition from AV to EDR solutions is fluid these days. Anti-virus products, such as EDR, have malware detection and defence capabilities that go far beyond simply searching for malware signatures.
EDR (Endpoint Detection and Response) solutions have been developed to provide more comprehensive protection for end devices such as laptops and servers. EDR solutions rely on functions such as behaviour-based detection, which enables them to detect even unknown threats. In addition, EDR has incident response and forensics capabilities to help organisations investigate and handle security incidents. While AV products focus on the detection of malware based on behavioural anomalies and signatures, EDR attempts to detect a compromise by combining various security mechanisms.
XDR (Extended Detection and Response) solutions are considered the next evolutionary step in security solutions. They go beyond EDR solutions by integrating multiple security technologies such as network security, cloud security and security information and event management (SIEM) to provide a more comprehensive overview of the security status. XDR solutions can also automatically detect and respond to threats.
The Cortex XDR weak point
"Cortex XDR is a security platform developed by Palo Alto Networks that combines network security, endpoint protection and cloud-based threat intelligence to provide comprehensive protection against advanced threats. Cortex XDR uses artificial intelligence to detect and respond to cyberattacks in real time and can be integrated with other security systems to provide a unified view of an organisation's security posture." (ChatGPT, 22/01/2023)

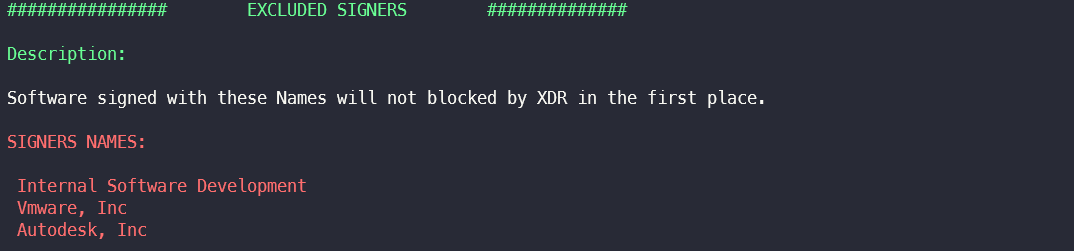
In April 2022, the security researcher published mr.d0x a blog post in which he describes how the hash and the corresponding salt of the uninstall password of a Cortex XDR agent from a Lock Database(LDB) can be extracted. If this hash were to be cracked, an attacker would be able to easily uninstall the Cortex XDR Agent and thus further compromise the affected system unhindered and without the risk of being detected.
Mr.d0x has thus found a vulnerability and described its exploitation in his blog post, which posed a considerable risk to the security of individual systems or even entire company networks.
Palo Alto did not publish a patch, but pointed out in a security advisory that a sufficiently secure password is sufficient to adequately counter this problem.
Our research on the topic has shown that the problem described by mr.d0x in his blog post goes beyond reading the hash and the corresponding salt.
Further development of the mr.d0x approach
Based on the previous research by mr.d0x, we have developed a tool that extracts much more information, such as exception rules or activated modules, from the lock information file.
Responsible Disclosure
We launched this tool back in October 2022 via Responsible Disclosure to the Palo Alto security team. This blog entry has been postponed accordingly, giving the security team enough time to fix the problem.
According to Palo Alto, since the Agent version 8.1 It is no longer possible to extract sensitive information from the LDBs. Palo Alto has not published a security advisory on this.
Cortex XDR Config Extractor
Prerequisites
The tool was developed and tested on agent versions 7.8.0 and 7.7.4. There are different approaches for extracting the information for certain agent versions, which we break down below.
Agent version <7.8
For agent versions prior to 7.8, any authenticated user under Windows can generate a support file via the Cortex XDR console in the system tray. The LDBs can then be found in the generated zip file:
logs_[ID].zipPersistenceagent_settings.db[XXXXX].ldb
Agent version ≥7.8
Since agent version 7.8.0, support files generated by the console are encrypted and cannot be parsed by the tool, but there are two methods to access the unencrypted LDBs under certain circumstances:
Method I
With administrative rights on the Windows machine, the LDBs can be copied directly from the following directory:
C:ProgrammeDataCyveraLocalSystemPersistenceagent_settings.db[XX].ldb
Method II
Generated support files are not deleted regularly, so it is possible to find unencrypted support files from old agent versions in the following directories:
C:User[Username]AppDataRoamingPaloAltoNetworks Trapssupportlogs_[ID].zip
The tool currently extracts the following agent information:
Tool scope
Uninstall Password Hash & Salt
The hash and the salt can be used to crack the agent's uninstall password - this has already been done by mr.d0x demonstrates.
If the hash is successfully cracked, an attacker can simply deactivate and even uninstall the XDR agent on the system.
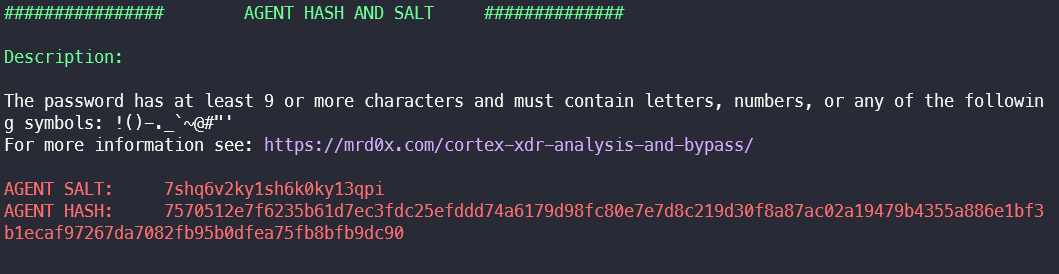
Excluded Signer Names
The Cortex XDR management platform can be used to store the names of software signers, which are generally stored on a Allowlist should land.
The names of the signatories for which an exception rule has been created are extracted in this section.
It should be sufficient to sign software with a self-signed certificate and the same name for the exception rule to apply. The actual certificates are not validated.
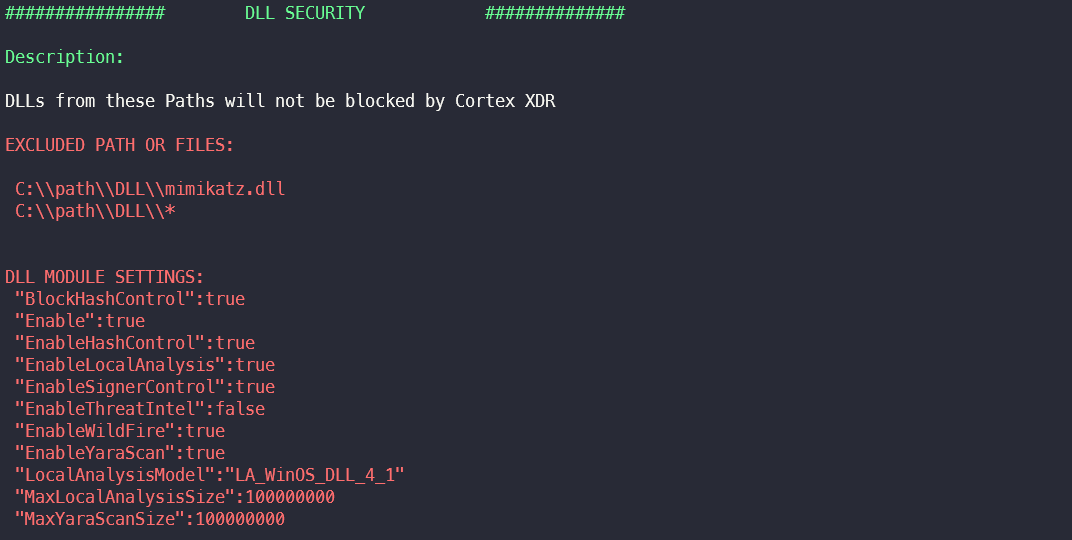
DLL Security Exclusions & Settings
In this section, files and paths for which an exception rule has been created in DLL security are extracted. Module settings such as the maximum file size for local scans or which sub-modules are activated are also displayed.
An attacker can use the paths from the exclusion to store a malicious DLL there, for example, and then use it via regsvr32.exe or rundll32 to be executed.
PE Security Exclusions & Settings
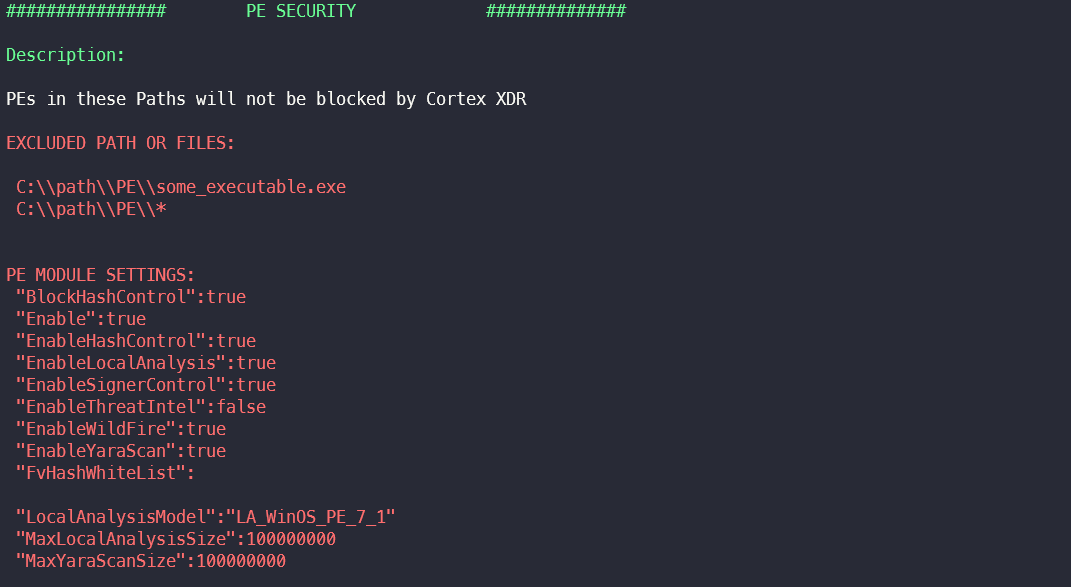
This section extracts files and paths for which an exception rule has been created in PE security. Module settings such as the maximum file size for local scans or which sub-modules are activated are also displayed.
An attacker can use the paths from the exclusion to store and execute a malicious executable there, for example.
Office Files Security Exclusions & Settings
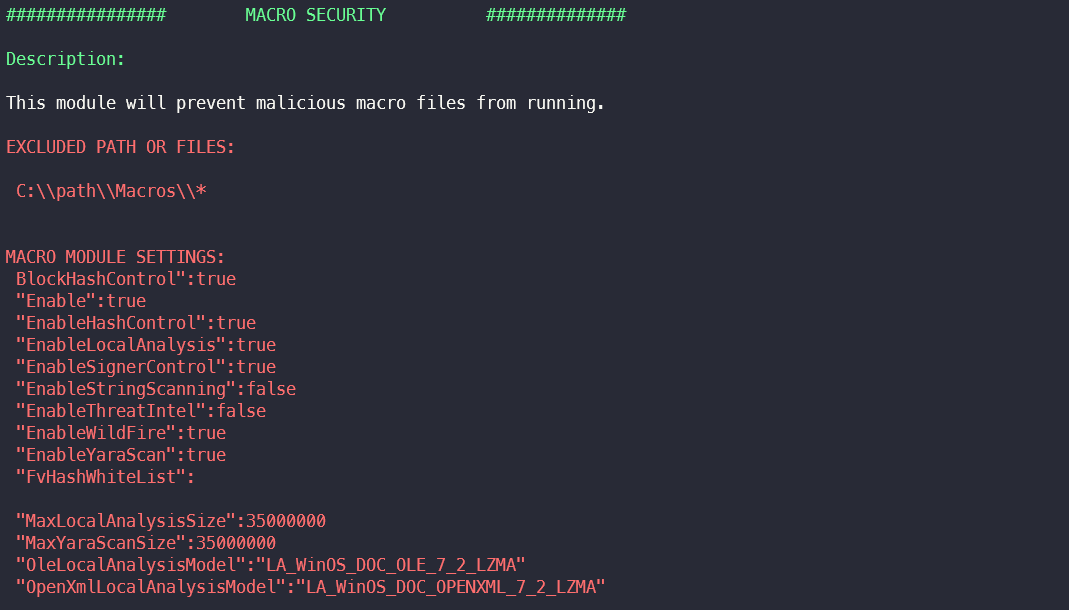
The module Macro-Security prevents the execution of malicious macro files. In this section, files and paths for which exception rules have been created in the module are extracted.
An attacker can use the paths from the exclusion to store and execute malicious Office files there, for example.
Credential Gathering Module Exclusions
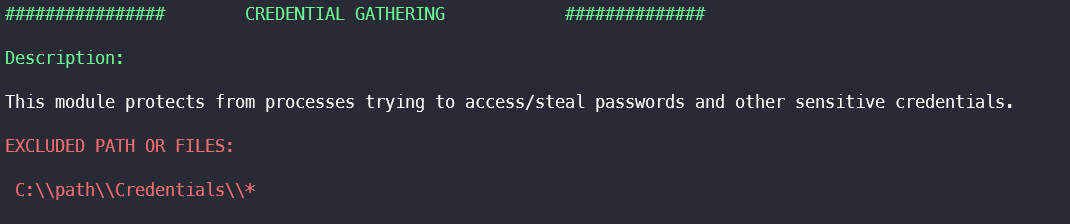
The module Credential Gathering protects against processes that attempt to access or steal passwords and other sensitive data. In this section, files and paths for which exception rules have been created in the module are extracted.
An attacker can use the paths from the exclusion to, for example, install malicious tools such as mimikatz or file scanner and execute it.
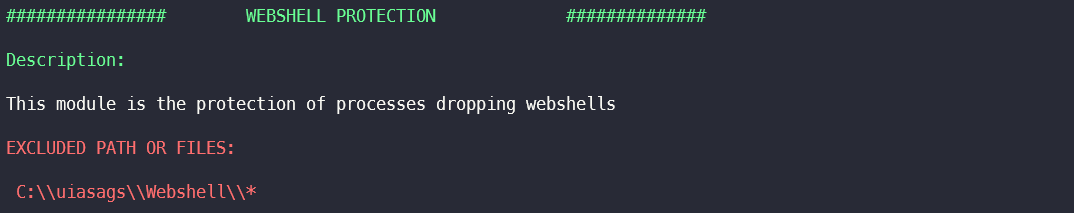
Webshell Protection Module Exclusions
The module Webshell Protecton is used to protect processes that send webshells. In this section, files and paths for which exceptions have been created in the module are extracted. These are usually processes that are allowed to store files with the file extensions php, asp, aspx, js etc.
An attacker can use the paths from the exclusion to store web shells there, for example, which can then be executed by a web server.
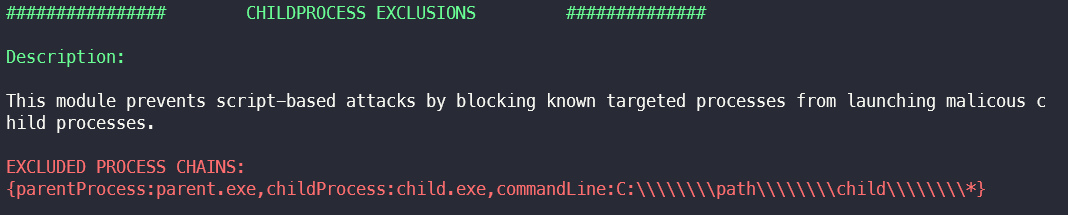
Childprocess Executions Exclusions
The module Childprocess Executions prevents script-based attacks by preventing known target processes from starting malicious child processes. In this section, process chains for which exception rules have been created in the module are extracted.
An attacker can use this information about authorised process chains to develop targeted malware that is not blocked by the XDR agent.
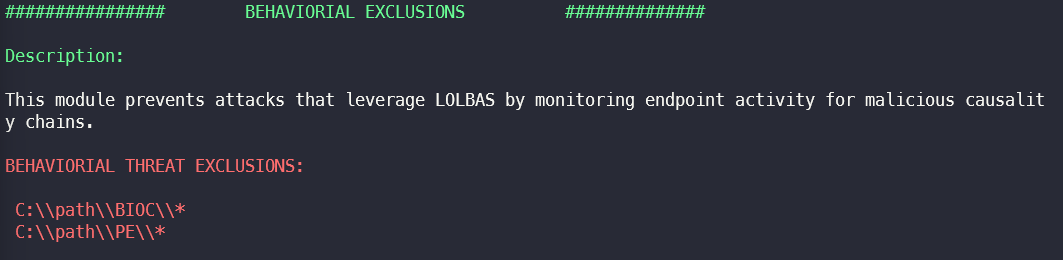
Behavioural Threat Module Exclusions
The module Behavioural Threat Prevention prevents attacks that, for example LOLBAS Binaries exploit by monitoring endpoint activity for malicious Causality Chains monitored. In this section, files and paths for which exception rules were created in the module are extracted.
An attacker can use the paths from the exclusion to, for example, store and execute tools there that would otherwise be blocked due to behaviour-based detection.
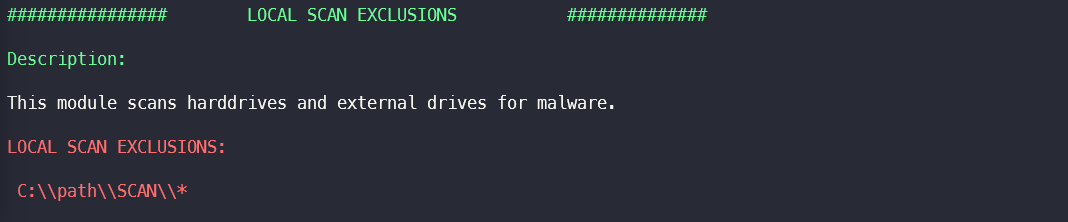
Local Malware Scan Module Exclusions
The module Local Malware Scan checks hard drives and external drives for
Malware. In this section, files and paths for which exception rules were created in the module are extracted.
An attacker can use the paths from the exclusion to specifically place malware there, which is then ignored by the local scan engine.
Memory Protection Module Status
This module attempts to control the working memory access of programmes such as mimikatz to prevent this. This section only extracts whether the module is activated.
An attacker can use this setting to assess whether memory protections are activated and, if necessary, use tools that access the working memory. For example, procdump.exe to dump the lsass.exe process to extract passwords (Link).

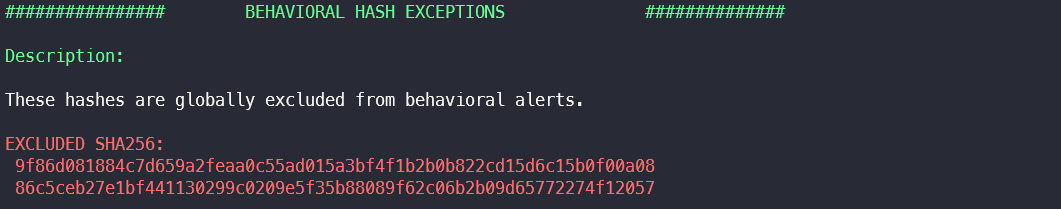
Global Hash Exclusions
In this section, all SHA-256 hash values for which a global exception has been created in Behavioural Threats are extracted.
An attacker can evaluate the hash values in order to use them to his advantage. It is possible that a general exception rule has been set up for a LOLBAS and can therefore be abused by the attacker.
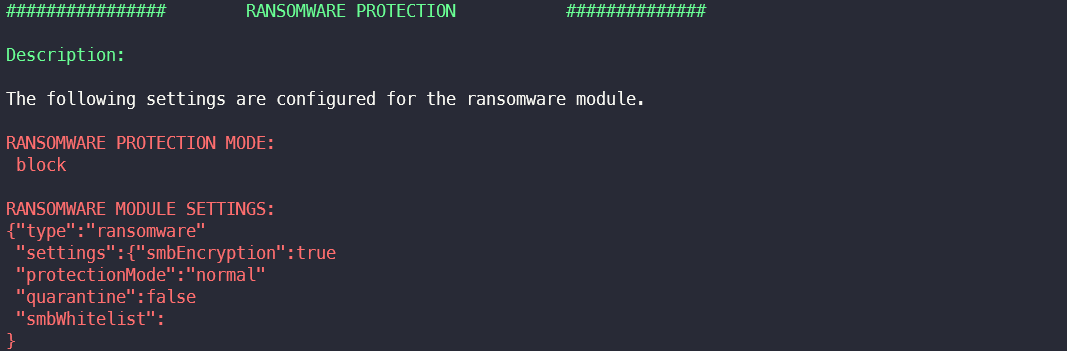
Ransomware Protection Module Mode & Settings
Module settings such as the ransomware protection mode or quarantine settings are extracted in this section.
An attacker can use this setting to assess which mechanisms are activated for ransomware and, if necessary, adapt his ransomware to circumvent any restrictions.
Conclusion
If someone were able to extract the settings and configurations of an XDR agent, this could have serious consequences for the security of an organisation. Agent configurations provide a comprehensive view of an organisation's security posture, as the settings and configurations control how the agent operates and how it detects potential threats. If an attacker were able to extract this information, they would have a detailed understanding of the organisation's security measures and could potentially bypass them.
In addition, an attacker could use the extracted information to develop targeted attacks that specifically exploit vulnerabilities in the organisation's security. For example, if an attacker knows the specific file types and actions that the XDR agent is configured to scan, they could create malware that is not recognised by the agent.